Cybersecurity for Confluence Users: A Complete Guide

We all have progressed from the days when we could leave our technological devices unlocked. Leaving our devices unprotected because we trust other people won’t cut it anymore. This is because as the world develops, cyber crimes increase. So, there is a need to be cybersecurity-conscious.
We have put this blog post together to help your organization and team stay ahead of bad actors in cyberspace. The blog post will examine cybersecurity, the basic principles, threats, and how to protect your data from cyber attacks. Likewise, it will provide examples of cybersecurity tools, how to handle cyber attacks, and outline a few cyber incidents that some companies have previously encountered.
The Basic Principles of Cybersecurity
Cybersecurity rides on and functions based on specific needs. These principles are put in an acronym – CIA. Let’s take a look at them.
Confidentiality
Confidentiality means keeping data secure from unauthorized access. It also extends to the non-disclosure of information to outsiders. For example, you should not share data like names, passwords, addresses, and other crucial information on a database with restricted parties.
To maintain confidentiality, ensure to follow some cybersecurity steps. Only share data with trusted sources, use passwords, encrypt data, etc.
Integrity
Integrity in cybersecurity means that your organization does not make changes to data without authorization. Therefore, you must maintain data accuracy. Likewise, data integrity requires you to monitor all modifications made by authorized users.
Availability
Availability is making data available to authorized individuals when needed. This means authorized users must have the passwords, decryption keys, etc., that will give them access to data.
How to Secure your Organization from Cyber Attacks
Here, we shall discuss some ways you can protect your data from cyber attacks.
Invest in Staff Training
According to the Security Online Magazine, humans are the weakest link when creating a cyber-safe environment. So, to strengthen this link, you must train your staff on what cybersecurity is. That is, they must be cybersecurity-aware.
As you plan to train them with the newest technological tools and build their capacities on the job, do not forget cybersecurity awareness training in your company calendar.
Show them the right way to create passwords, how to identify fake websites, how to identify phishing links, etc. This step is crucial when thinking about how to protect your devices from cyber attacks.
 Quick Tip
Quick Tip
Did you know that you can use Confluence for your cybersecurity training?
With izi LMS for Confluence, you can create a cybersecurity awareness course right in Confluence. And your employees will be able to go through training at their own pace without leaving their workspace – Confluence.
Maintain a Strict Password Policy
Sticking to a password policy you and your employees cannot compromise is suitable for your business. Ensure that everyone in your organization creates a minimum of eight characters and complicated passwords.
They must not create passwords from personal information that hackers can guess. The list includes a pet, favorite dish, hometown, etc. Likewise, use a password manager from a trusted company.
Update Software
Always remember to update all software you use in your organization. Check for updates manually if your software won’t update automatically. This helps to fix vulnerabilities and bugs in the software. On top of that, you get to access new features and enjoy enhanced performances.
Restrict Access
Not everyone in your company should have access to premium information. Limit the number of people you share sensitive information with. Likewise, do not hand over the encryption key or password to every employee. Just a few authorized persons are okay.
Use an Antivirus
An antivirus wards off malware infection from your systems. It detects and deletes malicious codes from your devices. This way, you wouldn’t have to worry about a malware attack, Ransomware attack, or other attack types.
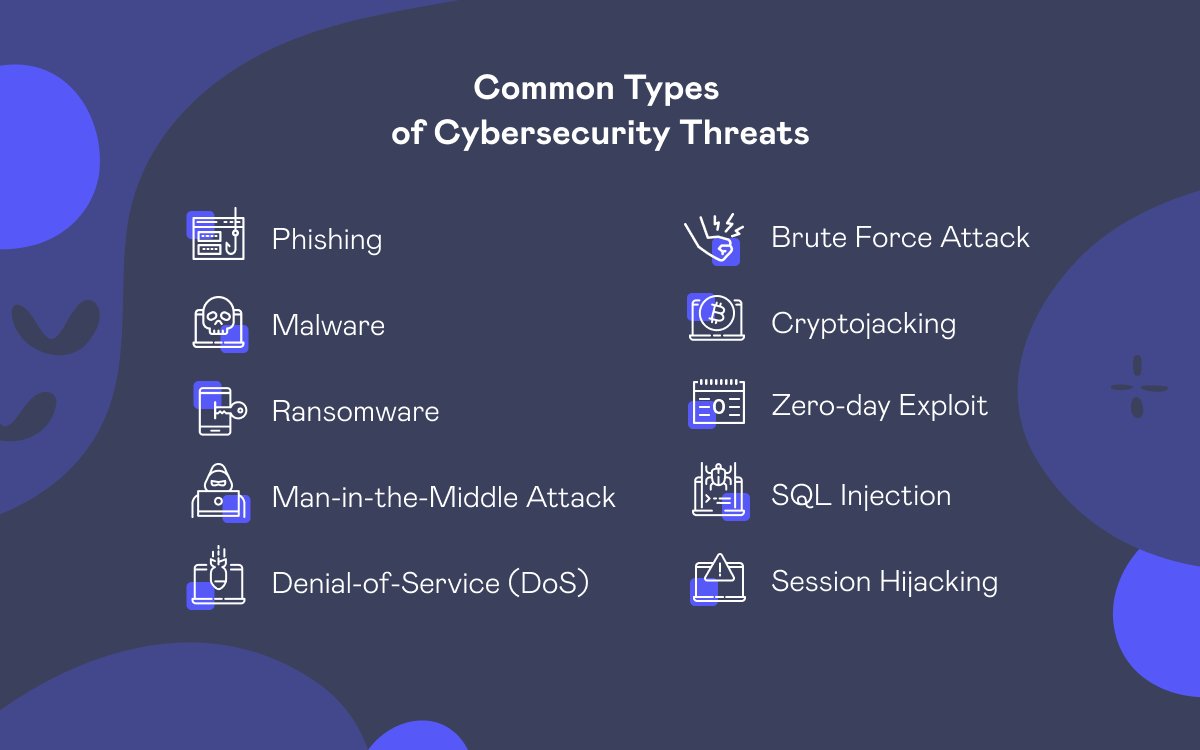
10 Common Types of Cybersecurity Threats
Cybercriminals have an arsenal from which they fire diverse attacks. These common cybersecurity attacks can disrupt workflows, lead to financial loss, cause reputation damage, etc. However, as many as these attacks are, we shall stick to only 10 of them in this blog post.
- Phishing
- Malware
- Ransomware
- Man-in-the-Middle Attack (MITM)
- Denial-of-Service (DoS)
- Brute Force Attack
- Cryptojacking
- Zero-day Exploit
- SQL Injection
- Session Hijacking
Phishing
Cybercriminals launch phishing attacks by sending fraudulent emails. They send those emails from fake addresses that appear as real ones. For example, the sender could be Yah00.com instead of Yahoo.com.
This way, the receivers will think the email is from a trusted source. Such emails often contain links or files that redirect the receivers to illegitimate sites where they will have their data stolen.
Phishers do not only target people through emails. They do so through texts, social media links, etc. Types of phishing attacks are vishing, spear phishing, pharming, and whaling.
Malware
This is malicious software designed to steal sensitive data from or damage a system. They are often delivered or shared over a network or system in a clickable or downloadable form.
Malicious software will install when users click or download the content (link or email attachment). Then, the software will begin to retrieve data from the computer’s hard drive. It can also destroy the system and deny a company’s network access.
Common types of malware cyber criminals use to infiltrate a system are; viruses, spyware, worms, adware, Trojan horses, and rootkits.
Ransomware
Ransomware is a type of malware, attackers launch by sending files that users believe to be safe and from trusted sources. The difference is that when users download and open these malicious attachments, the attackers can overpower a company’s network.
The bad actors achieve that by encrypting the data gathered. In some cases, they threaten to leak some of the information gathered. Following this, they demand ransoms. Then, they use the ransom payment as the basis for decrypting data or desisting from leaking them.
Man-in-the-Middle Attack (MITM)
Attackers launch man-in-the-middle attacks by positioning themselves between two communicating ends. This could be between user – application, email service provider – user, Wi-Fi – user, etc.
While in the middle, these attackers eavesdrop on personal information shared over a network. This personal information includes but is not limited to names, usernames, passwords, credit card details, and banking information. MITM attackers can also impersonate the entity a user interacts with, making it seem like everything is normal.
MITM attacks include Wi-Fi eavesdropping, email hijacking, IP (Internet Protocol) spoofing, and SSL (Secure Sockets Layer) spoofing.
Denial-of-Service (DoS)
A DoS attack crashes a system or network. When launched, it makes a network or system inaccessible to the users. Attackers use a single system to attack another single system.
When this happens, the victim organization’s administrators, members, and employees are locked out. Most times, DoS attacks do not cause financial or sensitive information loss. However, they often disrupt the victim’s activities and time & money to fix.
Brute Force Attack
We can call this attack the ‘guess it till you get it’ approach to knowing a password, an encryption key, or finding hidden pages on a website. Hackers who launch this attack use a lot of combinations to guess a password or key till they find the right one.
However, the length and complexity of the guessed password will determine how long it will take to guess the password. For instance, a four-digit password will be easy to crack and may take a few hours. On the contrary, a combination of 54 characters will take several hours to years to find out.
Cryptojacking
Now that cryptocurrency has become popular, we need to watch out for cryptojacking. Cryptojacking is accessing a user’s device illegally to mine digital currencies. Cryptojackers often launch this attack to dodge the risks associated with mining cryptocurrencies on their own.
Zero-day Exploit
A zero-day attack often follows an existing attack. Cybercriminals initiate this attack after learning about a previous attack on a software/application company or operating systems.
After that, they will begin to attack the users of those software/applications and operating systems. For instance, if iOS has been attacked, cybercriminals will take that advantage to attack iPhone users.
SQL Injection
In SQL injection attacks, cybercriminals make a SQL server vulnerable. By so doing, they can view any piece of data they cannot retrieve. Likewise, they can alter data or delete them from a database.
Cookie Hijacking
Websites drop cookies in your browser or hard disk to remember you when else you visit. Besides, they use it to store personal information about you and store your previous web activities. Knowing this, bad actors manipulate or forge cookies to steal users’ personal information.
Cybersecurity Tools that are Must-haves for your Organization
If you are ready to adopt all of the security measures listed above, you’ll need the required tools. In this section, we shall show you basic cybersecurity tools to use.
Password Management Tools
These tools will help your organization to store its numerous passwords. This way, your employees do not have to worry about forgetting their different login details. They only need to remember a single key to the password manager.
These tools are Kaspersky Password Manager, Zoho Vault, and LastPass Password Manager.
Antivirus Software
Antivirus software poses as the security guard always on the watch to secure your systems from all malware. It is one of the common cybersecurity tools most organizations use. Examples are Avast, Norton, and BitDefender.
Penetration Testing Tools
You have to think and act like one to prevent a hacker from penetrating your systems. These tools allow you to attack your company’s systems with the mindset of looking for vulnerabilities and fixing them. Use tools like Kali Linux, Wireshark, and Metasploit to test your systems for vulnerabilities.
Network Intrusion Detection Tools
The function of a network Intrusion detection software is to spot all forms of odd activities in your network. Software that helps you do this includes Samhain, OSSEC (Open Source HIDS (host-based intrusion detection system) Security), and AIDE (Advanced Intrusion Detection Environment).
Encryption Tools
In cybersecurity, encryption means storing data in an encoded form. That is, you can store sensitive information so that you can only view it but can’t read it. To read it, you’ll need an encryption key to decrypt the data. To do this, use tools like VeraCrypt, AxCrypt, and DiskCrypto.
Practical Ways to Respond to Cyber Incidents
Even after investing numerous resources into your company’s digital security, there is the likelihood of an attack. However, an attack should not be the end. Therefore, we shall outline how you can handle a cyber attack.
Containment
How to respond to a cyber incident first is to try to put everything under control. You do not have to panic or watch things go down completely. Check your servers to ascertain which one(s) was (were) attacked. Then, to curb the spread to other servers, disconnect them. Other things to do in this critical state are disconnecting from the internet and creating new passwords.
Assessment
At this stage, you need to find the cause of the attack to prevent future ones. For example, you want to know if a laptop was left unlocked, if it was an intrusion into your network, or if an employee shared an encryption key with an unauthorized person.
In short, you must assess which server was attacked, the angle of attack, the active network connection when the attack launched, and who else was attacked. Getting answers to these requires deliberate efforts from you.
A few ways to get answers is to reach out to providers of certain software/services you use. In addition, your data log or IDS (Intrusion Detection System) can also provide you with some answers. Finally, hire a cyber investigator to find out all related information to the breach if you do not have one.
Informing
It is time to communicate with every stakeholder in your company about the attack. Talk to the board, employees, and customers about it. Tell them how long ago the compromise happened, what you’re doing to fix it, and when your systems will be running again.
Real-life Examples of Cybersecurity Attacks
Cyber attacks are real. Research shows that about 66% of companies have been attacked this past year. So, here we shall discuss three of the biggest cybersecurity attacks in 2022.
Red Cross
Some hackers in January 2022 attacked a company that stores Red Cross’ data. The attack led to the data theft of 515,000 members of the Red Cross and Red Crescent Societies.
com
This cryptocurrency company experienced a breach on January 17, 2022. The hackers targeted 500 crypto wallets. Also, they stole $18 million of Bitcoin and $15 million of Ethereum. Additionally, they weakened the company’s blockchain technology by bypassing its 2FA (Two-factor Authentication).
CashApp
An ex-employee of this digital payment platform breached its servers in April 2022. The employee was said to cause the breach for selfish gains. The hacker stole a minimal volume of personally identifiable information (PII), except for account details.
Conclusion
With the rate at which cyber criminals attack companies these days, cybersecurity is now a necessity. Your company must do all it takes to remain safe in cyberspace. It should invest in tools and hire personnel that can help it recover in cases of possible breaches.
Employee training is another important step that needs to be taken. Try izi LMS to organize your cybersecurity training inside your Confluence.