How to encrypt your Confluence or JIRA server disk

Why do you need to encrypt your Confluence or JIRA server disk?
Confluence and JIRA usually contain confidential information which can be commercially sensitive information or just your private data (of course, you don’t want to share it with other people). Data protection against loss and unauthorized access can be achieved by managing user access and using the TLS encryption protocol for accessing your Confluence and JIRA servers. Disk encryption helps to protect your data even if your server (especially if you use a virtual server) or its disks were stolen.
How to encrypt a disk in Linux
A lot of Linux distributives offer disk encryption (or user home directory encryption) during installation. But sometimes you need to encrypt your disks after installation, or you need to encrypt only one of your disks – in this case the unencrypted data can be used before your administrator enters the password to decrypt the encrypted data (this procedure is usually required after the server reboot). .
We’ll use LUKS to encrypt one disk on the server. You need to install a cryptsetup package on your Linux server, if it is not installed yet:
apt-get install cryptsetup
or
yum apt-get install cryptsetup
If you’re reusing a disk (here and below in this article it will be ‘sdb’) that contained important data, you can rewrite your disk with random data to destroy the information on it:
dd if=/dev/urandom of=/dev/sdb
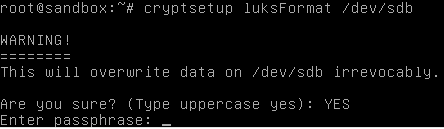
Let’s enable the /dev/sdb encryption. This irretrievably destroys all data on the disk:
cryptsetup luksFormat /dev/sdb
You need to confirm your actions by entering YES in the uppercase:
Then, you need to enter the password for the /dev/sdb decryption.
All data on /dev/sdb will be encrypted starting from this moment. But you also need to create a file system to start using an encrypted device on your server.
How to prepare an encrypted disk to use it on server
You need to open an encrypted device:
cryptsetup luksOpen /dev/sdb storage
where ‘storage’ is the device name that will be used in the system (/dev/mapper/storage). You need to enter the decryption password at this step.
Let’s format the disk before the first use:
mke2fs -j /dev/mapper/storage
You need a mount point to use the disk. Let’s create it:
mkdir /storage
After that, just mount your drive and start using it.
mount /dev/mapper/storage /storage
What happens after server reboot?
After reboot, your /dev/sdb will be unmounted and encrypted. You need the commands below to decrypt and mount your drive and start working with it:
cryptsetup luksOpen /dev/sdb storage mount /dev/mapper/storage /storage
The drive will be decrypted, mounted and ready to go.
How to encrypt Confluence or JIRA data
If you want to encrypt your Confluence or JIRA instance, you just need to install them into the /storage directory, also you need to place the Confluence or JIRA home directory there as well. If your instance is already installed – you can move your Confluence or JIRA files into /storage and change the startup scripts settings and Confluence or JIRA home settings in configuration. Your data will be encrypted. Don’t forget to set up correct user permissions for the moved files using ‘chown’.
Please note that a significant part of settings and all text content of your Confluence or JIRA instance are located in the database. The file system of your server contains major Confluence or JIRA system settings, attachments, exported data and backups. To be sure your instance is fully protected, you need to setup your database encryption. The most popular databases (MySQL, PostgreSQL, Oracle, SQL Server) support encryption to protect your data.
Some automation magic
It is insecure to set up automatic disk decryption and mounting, but it is annoying to enter a lot of commands in server console every time after restart. This problem can be solved by simple actions:
- disable automatic startup for all services that use an encrypted drive (Confluence, JIRA and so on)
- create a simple script to decrypt and mount the drive with data and starting related services (below you can see an example script to decrypt and mount the drive into /storage and then start Confluence and JIRA instances)
cryptsetup luksOpen /dev/sdb storage mount /dev/mapper/storage /storage /etc/init.d/confluence start /etc/init.d/jira start
Such script can simplify the start process for your encrypted Confluence or JIRA instances after the server reboot. You just start the script and enter your drive decryption password, and the automation magic does the rest.